What is encryption?
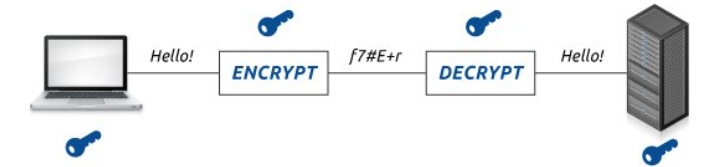
Encryption is the process of scrambling data so that it becomes very difficult to unscrambleand understand without the correct key.
This allows information to be sent from one person to another person, without having to worry about others intercepting and understanding the message.

History of Encryption
Keeping messages secret has been necessaryfor thousands of years!
The earliest known use of cryptography is found in non-standard hieroglyphs carved into monuments in Egypt.
Encryption was used in WW2 to send messages between allies in a way that could not be understood by the enemy.

Encryption in the modern world
Encryption matters to you – not just intelligence officers and computer scientists.
Encryption is used in the following areas that affect you:
- Technical (wireless networking)
- Political (defence and security)
- Social (Electronic messages)
- Economical (banking and Internet shopping)
There are 7 billion people in the world.. Images what it would be like if anyone could collect and read information about you.. Even things you wouldn’t want to share with anyone!

Encryption – Key Terms
Plain text: Data that has not been encrypted and can be understood
Cipher text: Data that has been encrypted and cannot be understood.
Cipher: An algorithm used to encrypt or decrypt the data.
Key: Sometimes used along with the cipher
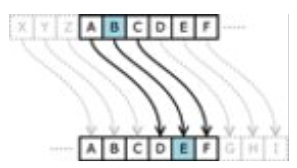
Caesar Cipher
The Caesar Cipher using a system whereby each letter of the plain text message is ‘shifted’ to change to another letter.
A ‘key’ is used to determine how many places each letter is to shift.
For example, if the key is 2 then the letter A becomes C, the letter B becomes D etc.
The word ‘HELLO’ encrypted with the Caesar cipher shift of3 is EHOOR.
Can you think of any ways to make the Caesar Cipher more complex so that its more difficult to decode a message? Think about what you could do to the key.
Pig Pen Cipher
The Pig Pen Cipher is a simple substitution cipher.
The letters are replaced by symbols which are determined by the position of the letter in a grid.
One such ‘grid’ is to use the position of letters on a mobile phone key pad.
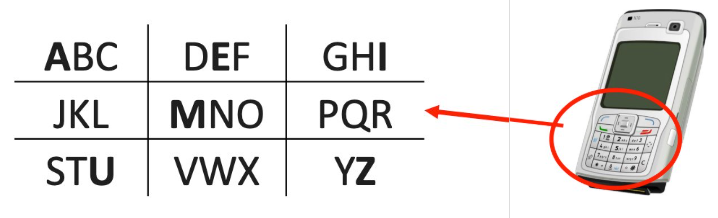
To write the letter A using the pig pen cipher we first draw the visible part of the grid that holds the letter.


We then place a dot where the letter is located – Either on the Left, Center or Right. In this case A is the first letter so we place a dot on the left.
Example letters:

The word ‘HELLO’ encrypted withthe Pig Pen Cipher is:
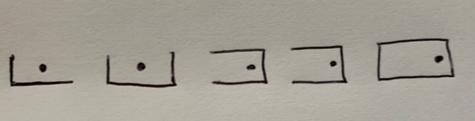
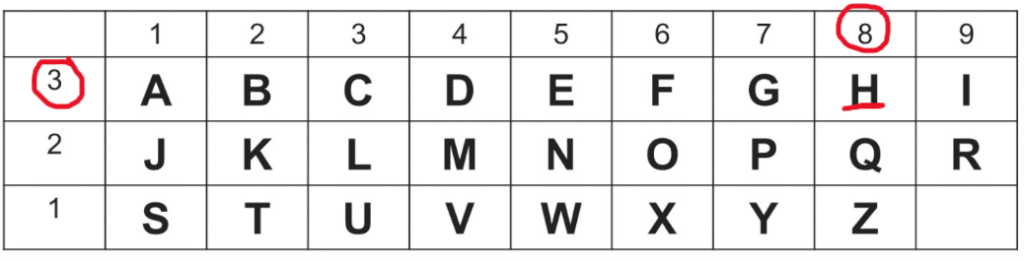
Viking Cipher
The Viking Cipher uses a system where by we have a central trunk and branches on either side are used.
The branches on the left determine which row the letter is in.
The branches on the right determine the position of the letter within the row.
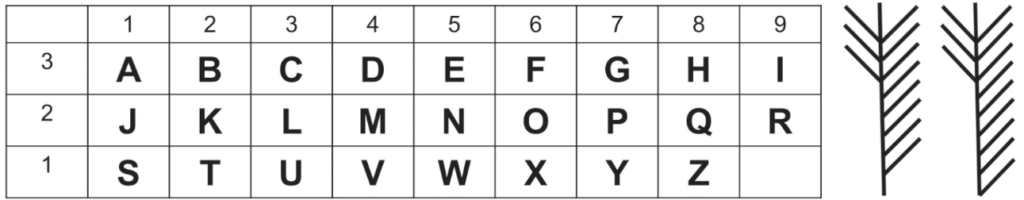
The word “Hello” is shown below:

Notice how the first symbol has 3 notches on the left indicating row 3.
We then have 8 branches on the right indicating column 8.
Using the table above we can see this is the H of the word Hello